An anomaly detection system for reliably detecting low-rate DDoS attacks
Introduction
Modern society's dependence on computer networks (such as the Internet) is getting stronger and stronger, so the importance of network security is self-evident. In terms of network security, detecting distributed denial of service attacks (Distributed Denial of Service, DDoS) has always been an important research content. There are two types of systems in intrusion detection: host-based intrusion detection system (IDS) and network-based IDS. Network-based IDS takes network traffic as the detection object, and it can be divided into two categories: misuse detection and anomaly detection. Misuse detection is based on the signature database of past attack events, so IDS of misuse detection can accurately detect old-style attacks. Misuse detection is ineffective against new variants of DDoS attacks, because the new features of the new variants of DDoS attacks are not yet in the feature library, so 100% of misuse detections can be avoided. This work is anomaly detection.
Anomaly detection is suitable for new variants of DDoS attacks. However, if the abnormal traffic is judged to be normal, a false alarm will occur. For an alarm, what is the probability of identifying abnormal traffic as abnormal? What is the probability of missed reports? These are reliable alarm problems for anomaly detection, as well as difficult problems for anomaly detection. The so-called reliable alarm means that the anomaly detector used has such characteristics in principle, and the user can preset the alarm probability and the probability of missed reports. Reliable alarm is the main feature of IDS studied in this article.
The basic characteristic of traditional DDoS attacks is that the data rate is particularly high. Therefore, IDS is often detected at a high rate, including previous work. In recent years, a low-rate DDoS attack has emerged, the purpose of which is to evade conventional IDS. Therefore, how to reliably detect low-rate DDoS attacks has become a meaningful study. This paper proposes an IDS that reliably detects low-rate DDoS attacks. It consists of three parts: real-time collection module of network traffic; detection decision module; alarm module. For the entire system, the input is network traffic, and the output is an alarm signal for abnormal traffic. The main feature of the system is that it can make decisions and alarms according to the detection probability specified by the user.
1 Characteristics of low-rate DDoS attacks
The low-rate attack discussed here is that the attacker targets the TCP protocol and uses the RTO timer to create an interruption in the link, resulting in congestion in the TCP control mechanism. The data flow of the attack is a square wave with a certain period. The rate of attack traffic is low, but it has high attack efficiency.
In the TCP protocol, RTO is an important value. RTO is adopted to ensure that the network has enough time to recover from congestion. If the RTO is too large and packet loss occurs, TCP needs to wait too long to retransmit the packet, increasing the TCP packet transmission time. If the RTO is too small, it will cause unnecessary retransmissions, and at the same time it will incorrectly trigger the TCP timeout retransmission algorithm, which reduces the TCP sending rate and thus reduces the performance of TCP. The principle of the attack is described below.
Setting the RTO value of TCP to 1 s, the attacker created a running interruption at time 0. The TCP sender has to wait for 1 s to retransmit and double the RTO. If the attacker creates another operation interruption between 1 s and RTT, it will force TCP to wait another 2 s. The attacker can use the KAM algorithm to create similar operation interruption at 3 s, 7 s, 15 s, ... In this way, the attack can be performed at a very low average rate, causing the server to deny service to the TCP stream. It can be seen that if the DDoS cycle is similar to the RTO, TCP will always lose packets. As a result, the state of overtime retransmission has been unchanged, and eventually the throughput is almost zero. Therefore, the key to low-rate attacks is whether the attacker can accurately predict the RTO. In addition, the duration of the pulse is also important. Literature [5] pointed out that when l = maxi {RTTI} and T = RTO, the attack efficiency is very high.
In short, compared with high-rate attacks, one of the biggest characteristics of low-rate DDoS attacks is to concentrate on sending malicious data within a small time frame, so that the average rate of attack data flow is relatively small to avoid the detection of conventional IDS.
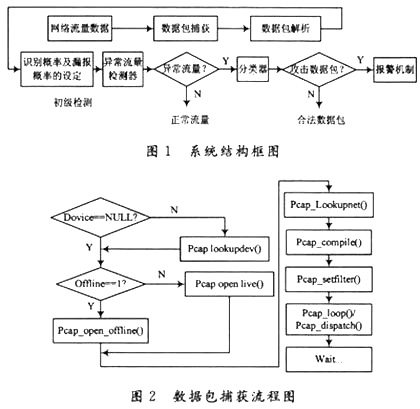
2 IDS structure and function
System structure and function
The IDS discussed in this article is mainly composed of three modules. The names and functions of each module are as follows:
Data acquisition and extraction module This module is based on the LIBPCAP function library. Encapsulated as C ++ class, it can be easily embedded in the intrusion detection system as a front-end flow collection and information extraction module. Considering that IDS is a type of real-time system, the design principle of this module is that the measured flow is sufficient for subsequent anomaly detection. For the system described in this article, information extraction is to extract packet length information from the measured data packets.
Attack recognition and decision module The user performs abnormal traffic detection according to the set recognition probability and missed report probability.
The alarm module alarms the attack in various ways according to the identification probability and false alarm probability set by the user. The system structure is shown in Figure 1. The structure of each module is described below.
2.2 Data collection and extraction module
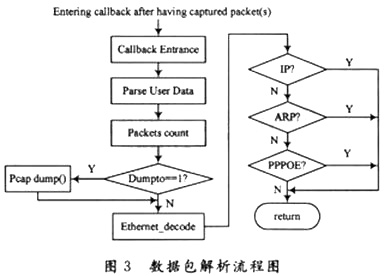
Network packet capture
The use of LIBPCAP function library to achieve network data packet capture, the library provides the main function functions (see LIBPCAP manual):
pcap_open_live (): Get the descriptor of the captured data packet, used to view the transmission of network data packets;
pcap_lookupdev (): returns the device pointer for pcap_open_live ();
pcap_open_offline (): Open the data packet file for offline analysis;
pcap_dump_open (): Open the file for writing data packets;
pcap_setfilter (): Set the packet filter program;
pcap_loop (): Start packet capture.
The data packet capture process is shown in Figure 2.
2.2.2 Data packet information extraction
After the packet capture is performed, the captured data packet needs to be parsed through the callback function. Therefore, when encapsulating the callback function, a parsing process must be used to achieve data sharing between the callback function and the thread class. Then, according to the hierarchy diagram of the TCP / IP protocol family and the definition of the data packet format of each layer, each layer adds The header and control information are decapsulated. See the literature [9] for the detailed process. FIG. 3 is the process of this analysis flow.
The above-mentioned real-time collection and information extraction module adopts a GUI-based reusable design method. The flow analysis result is output through the GUI interface, and the interface operation to the intrusion detection system is carried out to realize the next module: the preprocessing process of data collection and extraction of attack recognition and decision-making.
2.3 Attack Identification and Decision Module
There are two key issues in this module: one is to select the appropriate detection characteristics according to the recognition method; the other is how to achieve reliable recognition. Reliable identification means that the user can set the required identification probability and missed report probability in advance.
Let x (t) be the function of arrival flow. The minimum flow constraint function is recorded as f (I) (I> 0). Then in the interval [0, I], the cumulative flow reached will not be less than f (I) = min [x (t + I) -x (t)]. In the time interval [(n-1) I, nI] (n = 1, 2, ..., N), f (I, n) is the minimum flow constraint function in this interval. It is a random sequence of n. Divide each interval [(n-1) I, nI] into M segments. Each length is L. For the mth segment (m = 1, 2, ..., M), take the average value E [f (I, n)] m. Then when M> 10, E [f (I, n)] m conforms to the Gaussian distribution
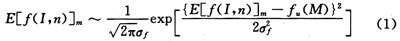
If the letter coefficient is set to 1-a1, the lower statistical limit is:
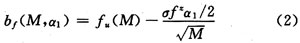
Thus, the template η = E [f (I, n)] is obtained. Let the threshold Vt = bf (M, α1), then the low-rate detection probability and the loss probability are:
Thus, the user can set the α1 value in advance to obtain a given detection probability and missed report probability. When η≥Vl, the data flow is regarded as normal.
2.4 Alarm module
After detecting a low-rate attack, IDS alerts the user and notifies the security management center of the event to make a defense decision. According to needs, alarm information can be sent to other networks to form a comprehensive and three-dimensional network security solution. The alarm methods that can be taken when an alarm message appears are: turn on the alarm light, pop up the interface, turn on the alarm bell, send a text message to the high-level decision-maker, send an email to the high-level decision-maker, etc. These types of alarm methods can be used alone or centralized Combine.
When the alarm appears, the security management center must be notified. If it is a serious large-scale attack, other networks should be notified to prevent the attack from causing extensive damage to the network; otherwise, internal processing.
3 Experimental results
Use the method described in the previous work to simulate the network traffic used in the experiment, and experiment with two data streams under normal and abnormal conditions, and make a comparison.
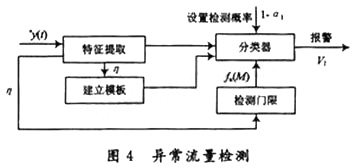
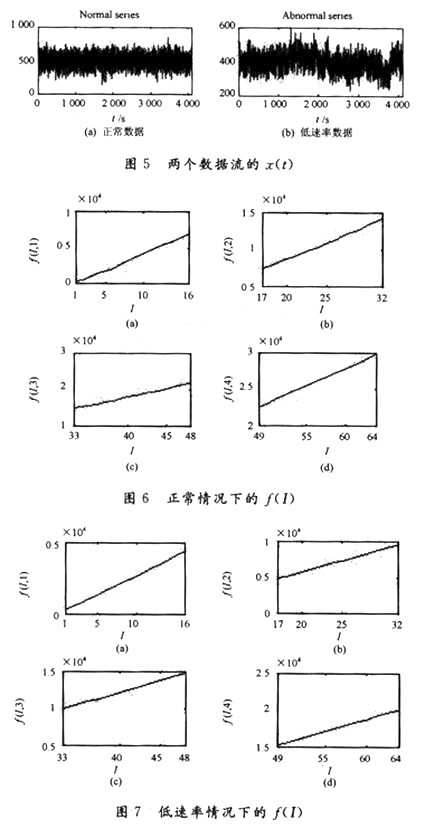
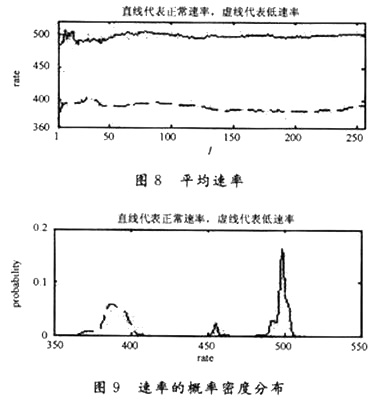
Fig. 5 shows the x (t) of the two data streams, and Fig. 6 and Fig. 7 show the f (I, n) (n, I = 1, 2, ..., 16) in both cases. Due to layout limitations, only the first four cases are given. Figures 8 and 9 are the average rate graph and the probability density distribution graph of the rate in both cases. It can be clearly seen that this method can accurately distinguish the low rate from the normal rate and can be used for low rate Attack detection.
4 Conclusion
A system for reliably detecting low-rate DDoS attacks is discussed, and simulation experiments are performed. Through the network data packet real-time collection and pre-processing of the information extraction module, the data packet is captured and analyzed, connected to the identification module, and an alarm mechanism is activated when an abnormality is found. The system can be set by the user to identify the probability of probabilities and missed reports. In addition to reliable identification, the system discussed in this article has an advantage. It can be easily extended to the hierarchical service network.
For example, suppose xip, j, k (t) are all data streams of the i-th class with priority p from connection j through server k, then the minimum flow constraint function is: 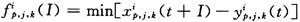 If it is used in Section 2.3, the entire system immediately becomes an IDS that specifically detects whether the incoming stream xip, j, k (t) is abnormal.
If it is used in Section 2.3, the entire system immediately becomes an IDS that specifically detects whether the incoming stream xip, j, k (t) is abnormal.
1KW-6KW Hybrid Inverter (with PWM Charge)

1KW-6KW PWM Hybrid Inverter,Lithium Battery Solar Inverter,AC 220V Solar Hybrid Inverter
suzhou whaylan new energy technology co., ltd , https://www.whaylan.com