Implementation of SOC high-speed data stream encryption transmission method
The development of computer technology has made mobile storage devices replace paper as the main way of information transmission, and paperless office has gradually become the main office mode for industry users. With the rapid development of modern industries such as e-commerce, digital management and mobile office, industry users (governments, enterprises, *, classified agencies) have higher and higher data security requirements for secure communication and mobile storage devices.
However, there are many security risks in mobile media. Random copying of data, arbitrary printing of data, loss of mobile media, etc. can lead to the disclosure or theft of information; *, the invasion of hackers completely exposes the transmission of Internet information to criminals. . Therefore, how to ensure the security of data during the process of information storage and delivery becomes a key issue for secure communication and mobile storage devices. The trend of replacing mobile storage devices with ordinary mobile storage devices is becoming more and more obvious.
At present, data stream encryption devices for secure mobile storage and secure communication mainly adopt software encryption or data segmentation encryption methods. These methods are low in security and can be easily broken. They are not suitable for the carrying, saving and transmission of important data by industry users with high security requirements such as government, *, confidential agencies and enterprises. Another solution for secure mobile storage devices is more secure, but it uses a method of CPU moving data in real time. Although this method is safer than the former method, its speed is greatly reduced, only 400KBps, which can not meet the speed requirement of 20MBps for mobile storage devices. In order to meet the market demand for high-speed real-time encryption in related fields, many research institutes and enterprises are striving to solve this problem.
Technical realization of high-speed data stream real-time encryption method
This paper introduces a high-speed data stream real-time encryption method. The method utilizes a hardware module in a chip to complete data encryption and high-speed transmission, and has higher security and faster transmission speed.
The chip architecture discards the traditional management method of data entry and exit controlled by the CPU, but uses the hardware modules in the SOC chip to implement the process of encryption and transmission. Each step is responsible for the special hardware module. The dedicated algorithm module completes the fast encryption of the data stream, and the high-speed transmission interface completes the data transmission, so that the large-volume data can flow truly and safely. Encryption is transmitted at high speed at the same time, realizing the real-time encrypted transmission of the data stream, meeting the speed and security requirements in the fields of secure mobile storage and secure communication.
1. Secure data stream transmission
The premise of realizing high-speed data stream encryption and decryption is to use high-speed communication interface and high-speed encryption and decryption module (Figure 1) to complete the process of receiving, encrypting/decrypting and transmitting data packets. The high-speed interface adopts a dual-port mode with the same flow direction, and the receiving and transmitting are separated (the high-speed interface can be USB2.0, SATA, PATA, Ethernet, etc.). The high-speed encryption and decryption module can adopt an algorithm with a relatively high security level and a speed comparison block, such as DES. 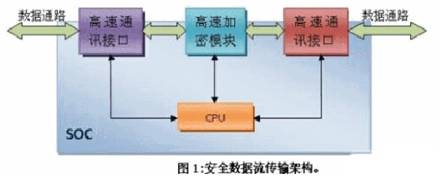
It can be seen from Figure 1 that the data stream flows from the high-speed communication interface to the chip, and after passing through the high-speed encryption module, it is sent out through another high-speed interface to complete a high-speed encrypted communication process.
2. Pipe line data processing
Although using a high-speed communication interface and a high-speed encryption module, each packet takes a certain amount of time to complete the three steps of receiving, encrypting/decrypting, and transmitting. If sequential execution is performed, the speed of such products is lower than that of The products with encryption function are much lower. In order to increase the encryption transmission speed again, the data processing method of Pipe line (Fig. 2) is adopted in the process of data encryption transmission, which can double the processing speed. 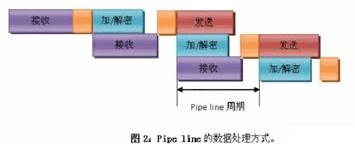
When processing a packet, the entire process is broken down into three parts: receive, add/decrypt, and send. The CPU only controls these three modules every time a step is completed, and no data processing is performed. When a large amount of data needs to be processed, one of the three data packets can be completed simultaneously in each time period, as shown in FIG. 2, that is, one data packet is processed in one time period, and the time period is a Pipe line period. However, it is necessary to ensure that all three steps are completed in one cycle, and the CPU can control these three modules.
As can be seen from Figure 2, the Pipe line data processing cycle is:
Tperiod = (Max(Ttx, Trx, Tsec) + Tsys)
In this process, if the processing time of the three stages is similar, the processing cycle is obviously reduced to about 1/3 of the original, and one packet is processed in one cycle, and the speed is increased by 2 times. The CPU only takes control of the task, is not responsible for the data handling, and the program quantity is very small, which greatly reduces the time taken by the CPU to execute the program.
3. Data storage domain switching
How to ensure that 3 packets can be processed separately in one processing cycle? This article uses the method of data storage domain switching. As shown in FIG. 3, each functional module corresponds to a RAM module, and receives the Ming/Ciphertext in the nth cycle and stores it in the RAM1; in the n+1th cycle, the RAM1 is switched to the encryption/decryption module. The data packet in the RAM1 is added/decrypted; in the n+2th cycle, the RAM1 is switched to the transmitting module, and the secret/cleartext in the RAM1 is sent out to complete the processing of the same data packet.
In order to realize Pipeline's pipeline working mode, three data packets are processed simultaneously in the same cycle. Receiving data to RAM1 in the nth cycle, adding/decrypting the data in RAM2, and simultaneously transmitting the data in RAM3; in the n+1th cycle, RAM1 is switched to the encryption/decryption module, and RAM2 is switched to the transmission module. And RAM3 is switched to the receiving module, and the three functional modules respectively process the corresponding data to ensure that one data packet is processed in one processing cycle on average, and the pipeline pipeline working mode is realized.
The implementation method draws on the way the CPU performs pipeline operations when executing instructions, and uses two high-speed communication interfaces to ensure that each module is working at every moment on the data stream. This method can make full use of all module resources, greatly improve the speed of data stream encryption, and make real-time encrypted communication and high-speed encrypted storage possible. 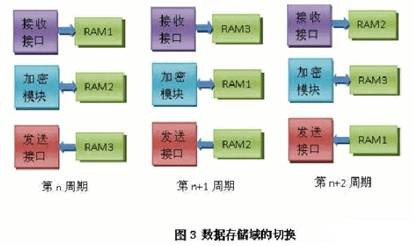
Technical highlights
The implementation of high-speed data stream encryption has the following technical highlights to meet real-time, high-speed, and security requirements.
(1) Add/decrypt and data transmission are completely realized by the chip, relying on the amount of code is very small, the hardware implementation is ten times or even dozens of times faster than the software implementation.
(2) Pipeline's pipeline architecture is adopted inside the SOC, so that three modules are executed in parallel in the same cycle, and three tasks are completed at the same time, which greatly shortens the average processing time of one packet.
(3) The traditional management mode of the CPU has been changed. It is only used as the control terminal of the encryption module and the communication interface, and is not in the path of data handling, and avoids taking too much time when the CPU executes the lengthy code.
(4) Two high-speed communication interfaces separate reception and transmission, and one packet can be received at the same time and another data packet can be transmitted.
(5) Internally integrate high-speed and high-security encryption algorithms to make data appear in the form of ciphertext to ensure data security.
Through actual detection and comparison of the method with the traditional encryption method, it can be clearly seen that the data stream encryption realized by this method is 50 times higher or higher than the traditional method, effectively solving the communication and mobile storage. The problem of significantly reducing the speed after adding a highly secure encryption algorithm provides reliable hardware and technical support for high-speed data stream encryption, high-security encrypted storage devices, and secure communication devices.
electric motorcycle charger
Electric Motorcycle Charger,Li-Ion Battery Charger For Motor,Motorcycle Li-Ion Battery Charger,Motorcycle Fast Battery Charger
HuiZhou Superpower Technology Co.,Ltd. , https://www.spchargers.com